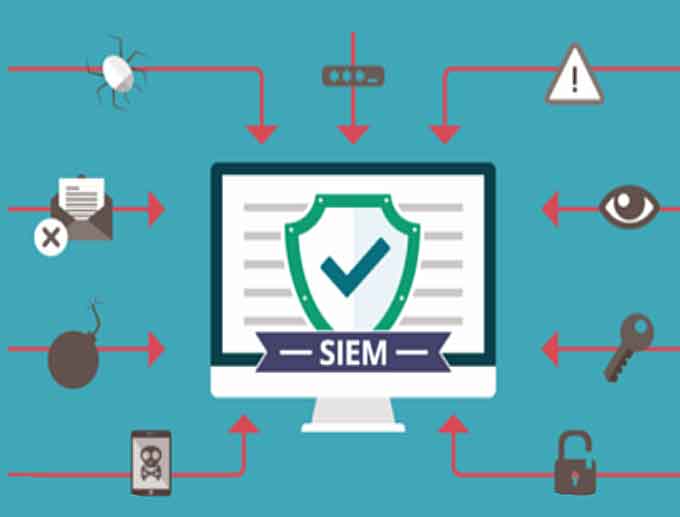
What is a SIEM?
Security Information and Event Management (SIEM) is a software solution that combines and analyzes activities from several different resources across the organization’s IT infrastructure. This system collects security data from network devices, domain controllers, servers, and more. SIEM stores, normalizes, aggregates, and does analytics to that data to look for new trends, detect threats, and enable companies to investigate alerts.
How Does SIEM Work?
SIEM provides two fundamental capabilities to an Incident Response team:
-Reporting and Forensics about Security incidents
-Alerts based on analytics that match a particular rule set, indicating a security issue
SIEM is a data aggregator, search, and reporting mechanism at its core. SIEM gathers massive amounts of data from the entire networked environment, consolidates it and makes that data easily accessible to humans. You can research data security breaches with maximum possible detail as needed with the data at your fingertips.
SIEM in the Enterprise
Some customers have learned that they need to maintain two separate SIEM solutions to get the best value for each purpose since the SIEM can be incredibly noisy and resource intensive. One for data security and the other for compliance.
Beyond Security Information Management system’s main use case of logging and log management, organizations use their SIEM data in various ways. One use case is to help show compliance or cooperation for rules or regulations like SOX, HIPAA, PCI, and GDPR.
SIEM tools also aggregate data that can be used for capacity management projects. You can track bandwidth and data growth with a timeline to plan for growth and budgeting purposes. Data is key and understanding the current usage in the capacity-planning world and trends eventually allows you to manage growth and prevent large capital expenses as a reactionary measure.
Limitations of SIEM Applications as a Full Data Security
SIEM applications provide only little contextual information about their native events, and SIEMs are generally known for their blind spot on unorganized data and emails. For example, you might notice a rise in the network activity from an IP address, but not be able to see the user that created the traffic or which files were accessed. In this case, the context may be everything.
What looks like a major transfer of data could be completely good and warranted behaviour, or it could be a theft of the huge amount of sensitive and critical data. A lack of context in security alarms leads to failure; eventually, the security will be desensitized to the alarm bells going off each time an event is triggered.
SIEM applications are not capable enough to classify data as sensitive or non-sensitive and therefore cannot distinguish between sanctioned file activity from suspicious one that can be damaging to intellectual property, customer data, or company security.
Ultimately, Security Information Management applications are only as capable as the data they receive. IT is mostly left chasing down false alarms or otherwise insignificant issues without additional context on that data. Context is essential in the data security world to know what to fight.
The biggest issue Cyber Security Consulting Firms hear from customers when they use SIEM is that it is extremely difficult to determine and research security events. The amount of low-level data and the high number of alerts cause mayhem, and users get a warning but the lack the clarity and context to act on that alert immediately.